Authentication Application Credentials
Description
Application-only access is broader and more powerful than delegated access (User Credentials), so you should only use app-only access where needed. Use it when: 1. The application needs to run in an automated way, without user input (for example, a daily script that checks emails from certain contacts and sends automated responses). 2. The application needs to access resources belonging to multiple different users (for example, a backup or data loss prevention app might need to retrieve messages from many different chat channels, each with different participants). 3. You find yourself tempted to store credentials locally and allow the app to sign in 'as' the user or admin. [API reference]
Instructions
Follow these simple steps below to create Microsoft Entra ID application with application access permissions.
- Navigate to the Azure Portal and log in using your credentials.
- Access Microsoft Entra ID.
-
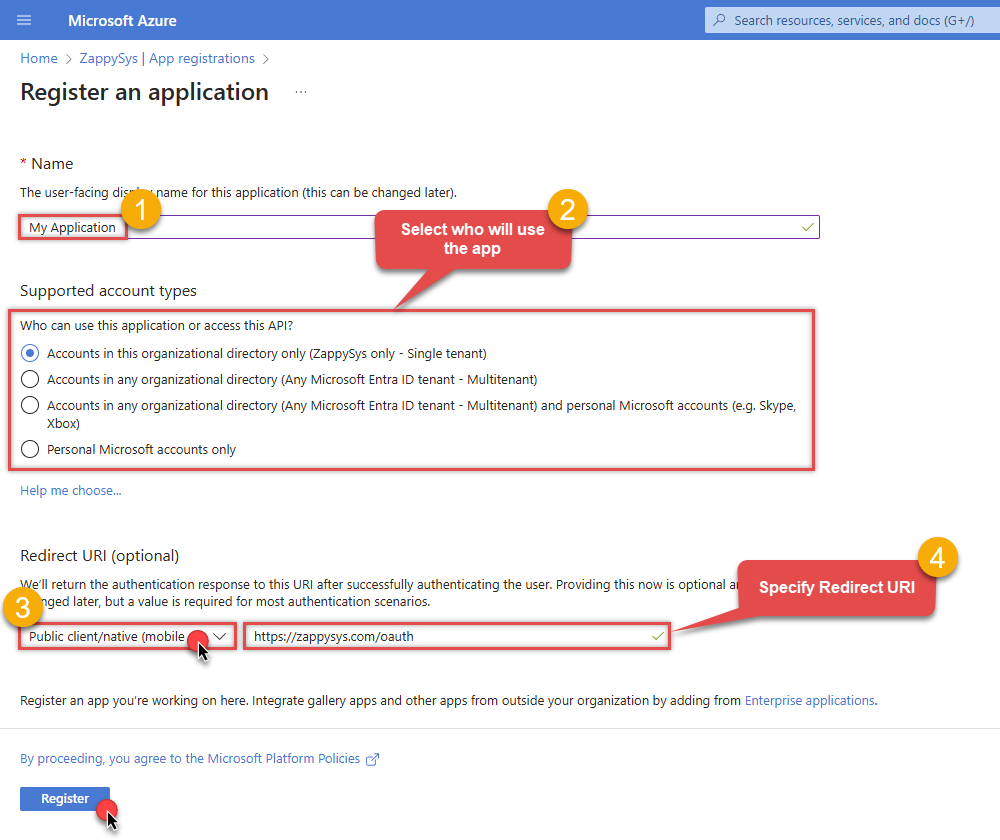
Register a new application by going to
App registrations
and clicking on New registration button:
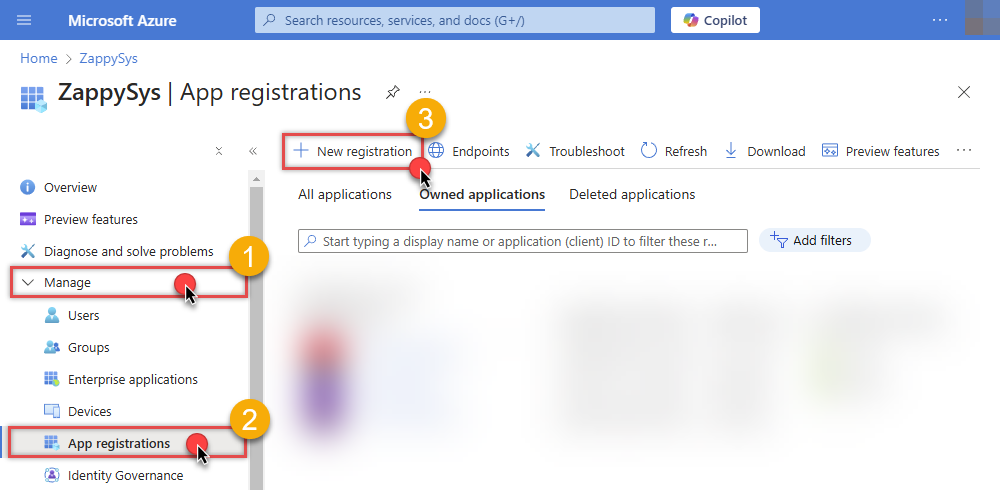 INFO: Find more information on how to register an application in Graph API reference.
INFO: Find more information on how to register an application in Graph API reference. -
When configuration window opens, configure these fields:
-
Supported account type
- e.g. select
Accounts in this organizational directory onlyif you need access to data in your organization only.
- e.g. select
-
Supported account type
-
Redirect URI:
- Set the type to
Public client/native (mobile & desktop). - Leave the URL field empty.
- Set the type to
-
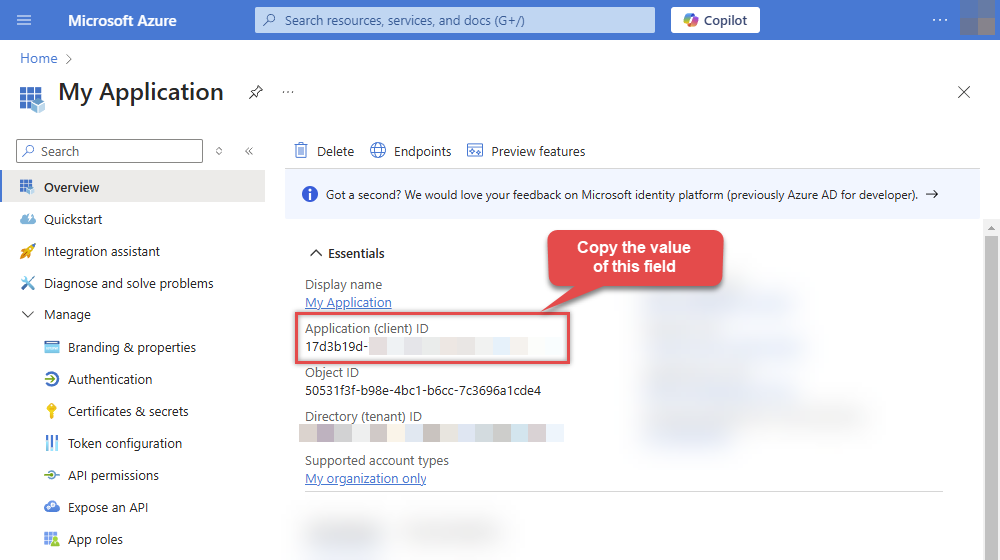
After registering the app, copy the Application (client) ID for later:
-
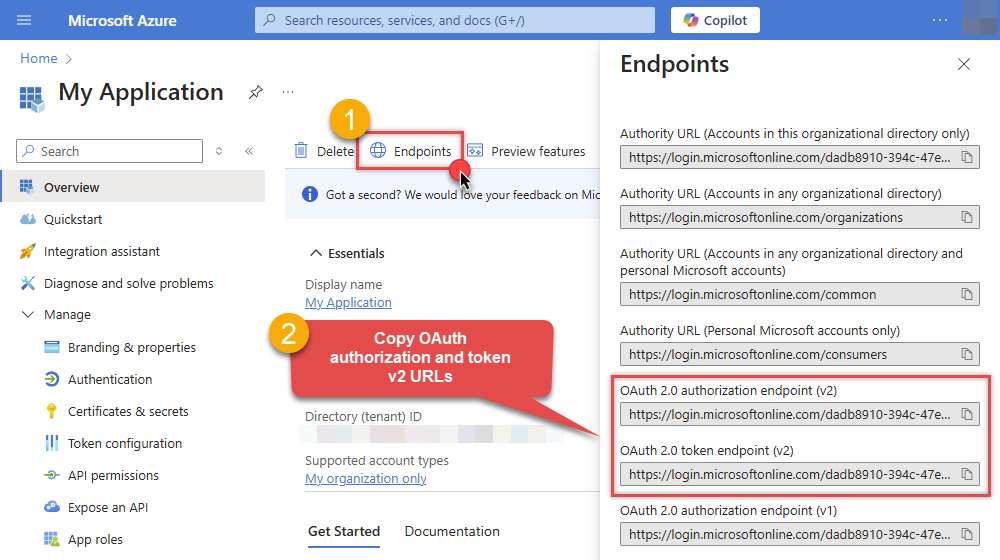
Then copy OAuth authorization endpoint (v2) & OAuth token endpoint (v2) URLs:
-
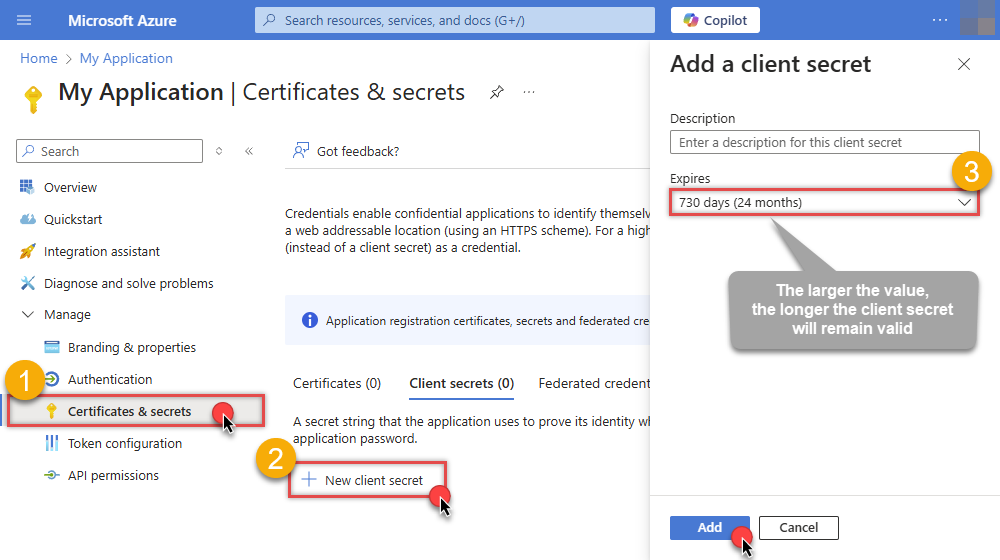
Continue and create Client secret:
-
Then copy the Client secret for later steps:
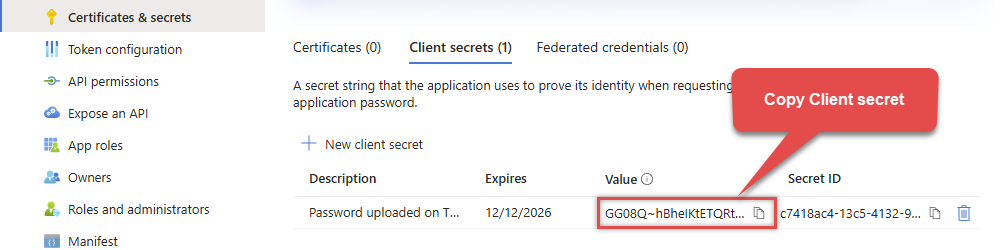
-
Continue by adding permissions for the app by going to the API permissions section, and clicking on Add a permission:
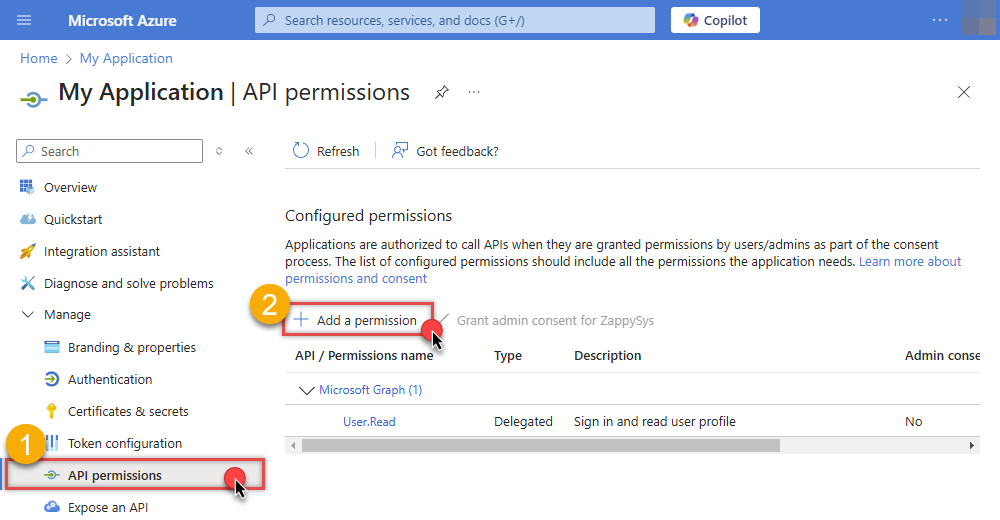
-
Select Microsoft Graph:
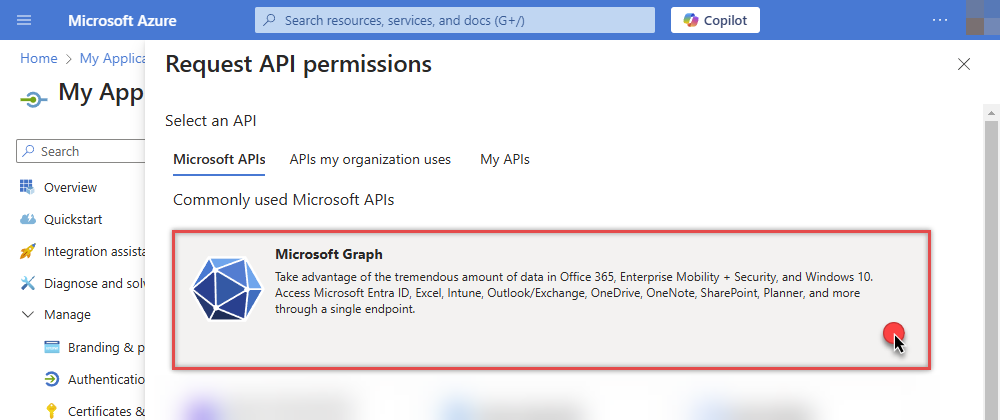
-
Then choose Application permissions option:
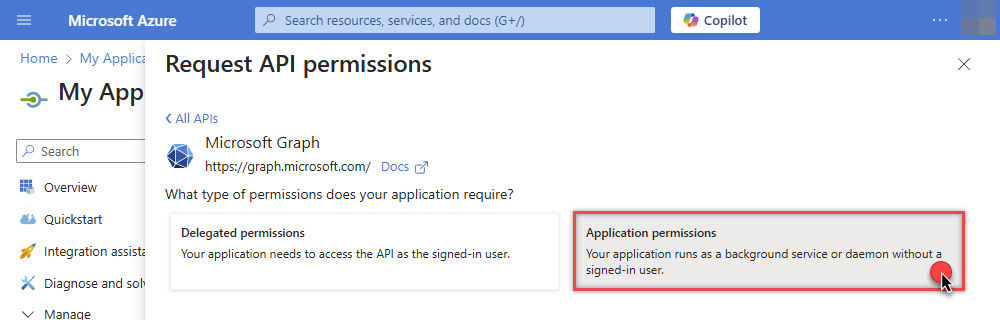
-
Continue by adding these Mail (Outlook) permissions:
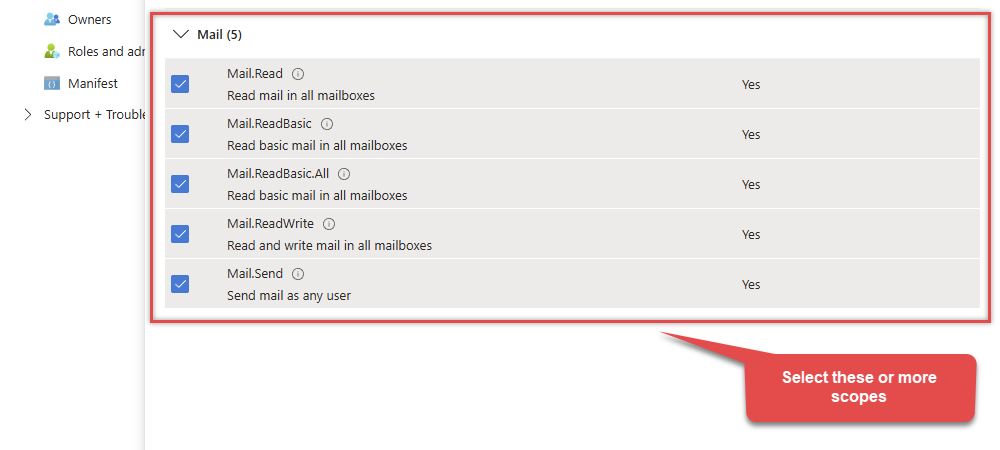
-
Finish by clicking Add permissions button:

-
Now it's time to Grant admin consent for your application:
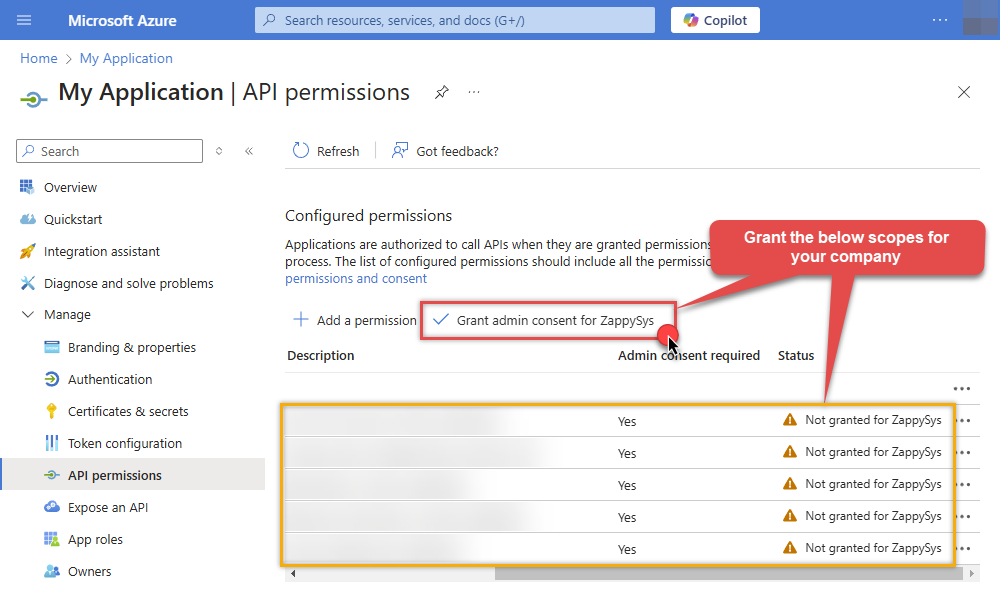
-
Confirm all the permissions are granted:
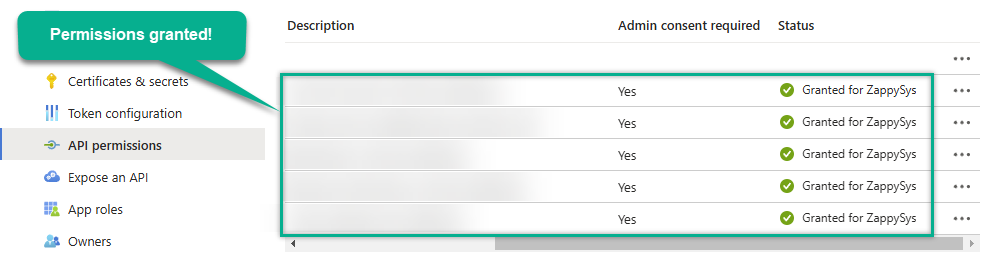
-
Now go to SSIS package or ODBC data source and use the copied values in Application Credentials authentication configuration:
- In the Token URL field paste the OAuth token endpoint (v2) URL value you copied in the previous step.
- In the Client ID field paste the Application (client) ID value you copied in the previous step.
- In the Client Secret field paste the Client secret value you copied in the previous step.
- Choose Default User Id from the drop down menu.
- Click Test Connection to confirm the connection is working.
- That's it! Now you can use the API Connector!
Parameters
| Parameter | Required | Default value | Options | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
|
Name:
Label: Token URL |
YES |
|
|||||||||
|
Name:
Label: Client ID |
YES | ||||||||||
|
Name:
Label: Client Secret |
YES | ||||||||||
|
Name:
Label: Scope Permissions you want to use. |
YES |
https://graph.microsoft.com/.default
|
|
||||||||
|
Name:
Label: Default User Id The Microsoft Mail user ID GUID or email address for the account to read messages from. (Examples: '4ff54a77-9c09-4274-958f-83bdc0a53900' or 'first.last@domain.com') |
YES | ||||||||||
|
Name:
Label: RetryMode |
RetryWhenStatusCodeMatch
|
|
|||||||||
|
Name:
Label: RetryStatusCodeList |
429|503
|
||||||||||
|
Name:
Label: RetryCountMax |
5
|
||||||||||
|
Name:
Label: RetryMultiplyWaitTime |
True
|
