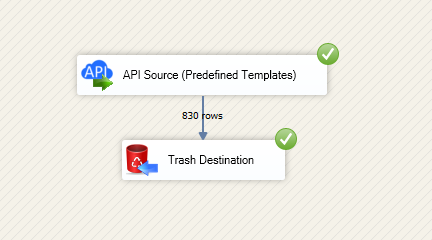
Reading data in SSIS
In this section we will learn how to configure and use OneDrive Connector in API Source to extract data from OneDrive.
Video tutorial
This video covers following and more so watch carefully. After watching this video follow the steps described in this article.
- How to download SSIS PowerPack for OneDrive integration in SSIS
- How to configure connection for OneDrive
- How to read data from OneDrive
- Features about SSIS API Source
- Using OneDrive Connector in SSIS
Step-by-step instructions
-
Begin with opening Visual Studio and Create a New Project.
-
Select Integration Service Project and in new project window set the appropriate name and location for project. And click OK.
In the new SSIS project screen you will find the following:
- SSIS ToolBox on left side bar
- Solution Explorer and Property Window on right bar
- Control flow, data flow, event Handlers, Package Explorer in tab windows
- Connection Manager Window in the bottom
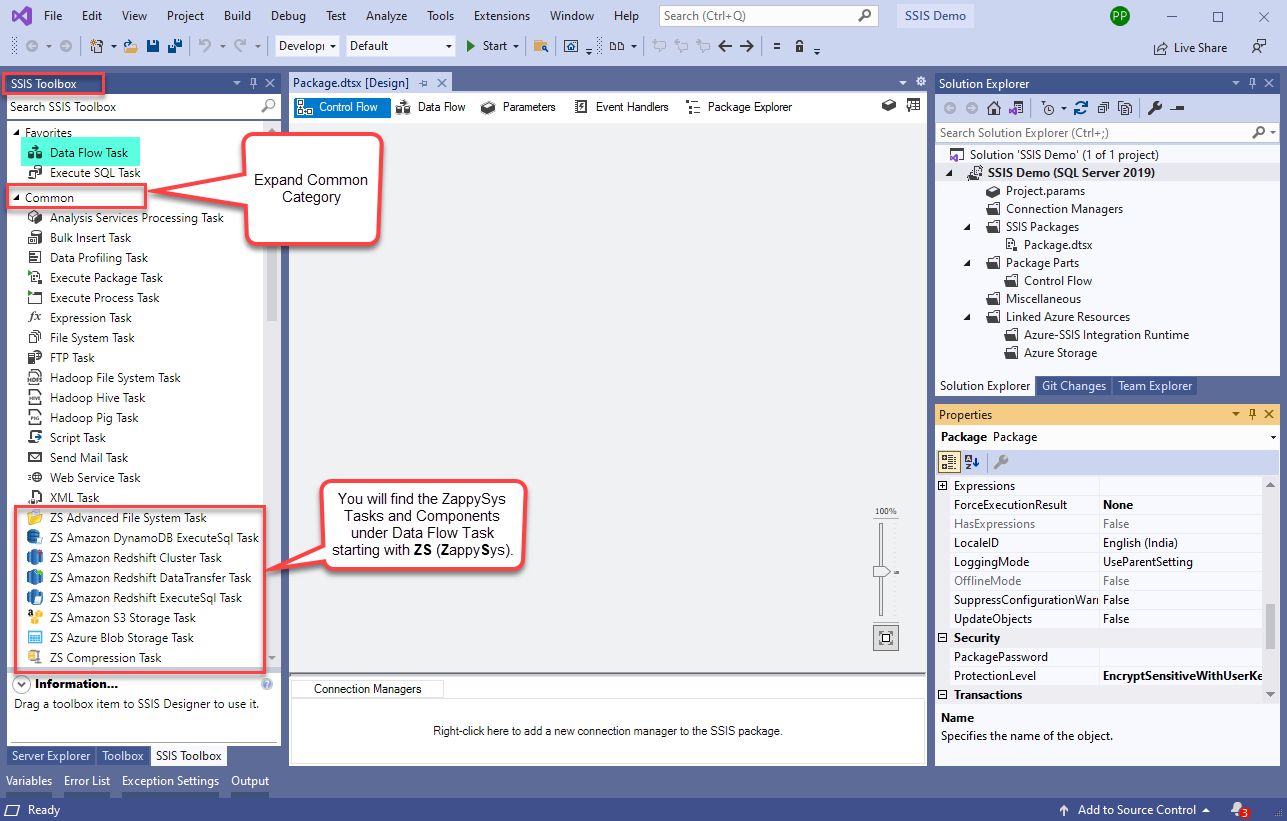 Note: If you don't see ZappySys SSIS PowerPack Task or Components in SSIS Toolbox, please refer to this help link.
Note: If you don't see ZappySys SSIS PowerPack Task or Components in SSIS Toolbox, please refer to this help link. -
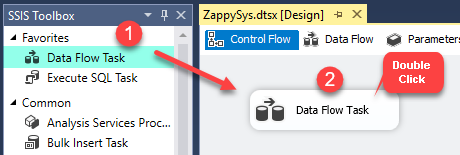
Now, Drag and Drop SSIS Data Flow Task from SSIS Toolbox. Double click on the Data Flow Task to see Data Flow designer.
-
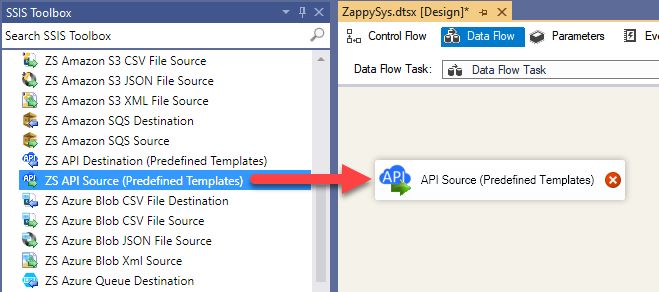
From the SSIS toolbox drag and API Source (Predefined Templates) on the data flow designer surface, and double click on it to edit it:
-
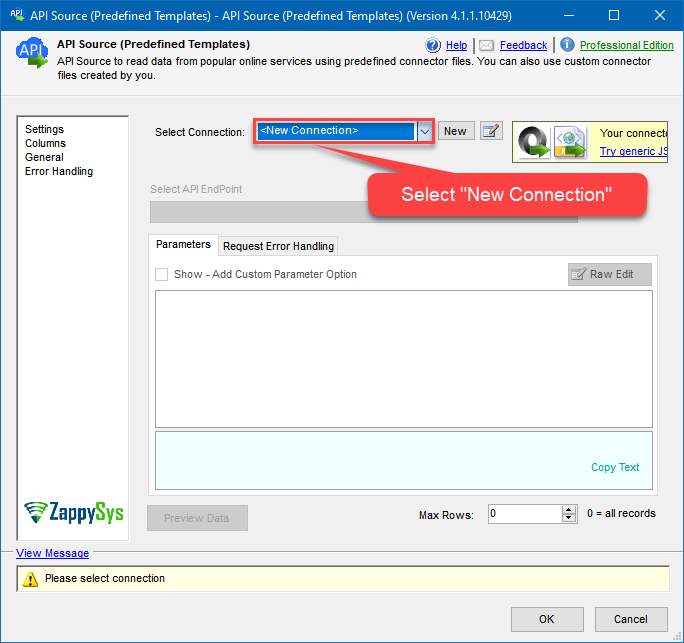
Select New Connection to create a new connection:
-
Use a preinstalled OneDrive Connector from Popular Connector List or press Search Online radio button to download OneDrive Connector. Once downloaded simply use it in the configuration:
OneDrive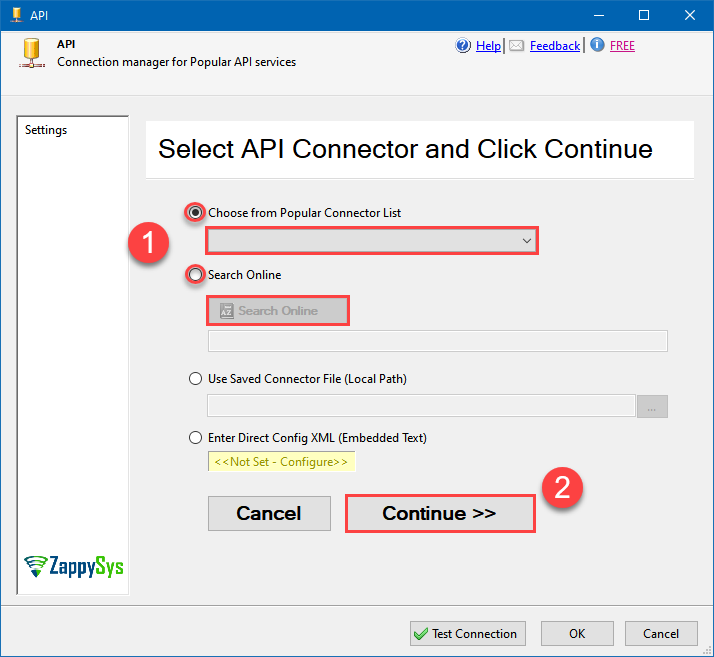
-
Now it's time to configure authentication. Firstly, configure authentication settings in OneDrive service and then proceed by configuring API Connection Manager. Start by expanding an authentication type:
OneDrive authentication
Use delegated access (User Credentials) whenever you want to let a signed-in user work with their own resources or resources they can access. Whether it's an admin setting up policies for their entire organization or a user deleting an email in their inbox, all scenarios involving user actions should use delegated access. [API reference]
Follow these simple steps below to create Microsoft Entra ID application with delegated access:
WARNING: To automate your company's processes, make sure you use a system/generic account (e.g.automation@my-company.com). When you use a personal account which is tied to a specific employee profile and that employee leaves the company, the token may become invalid and any automated processes using that token will start to fail.- Navigate to the Azure Portal and log in using your credentials.
- Access Microsoft Entra ID.
-
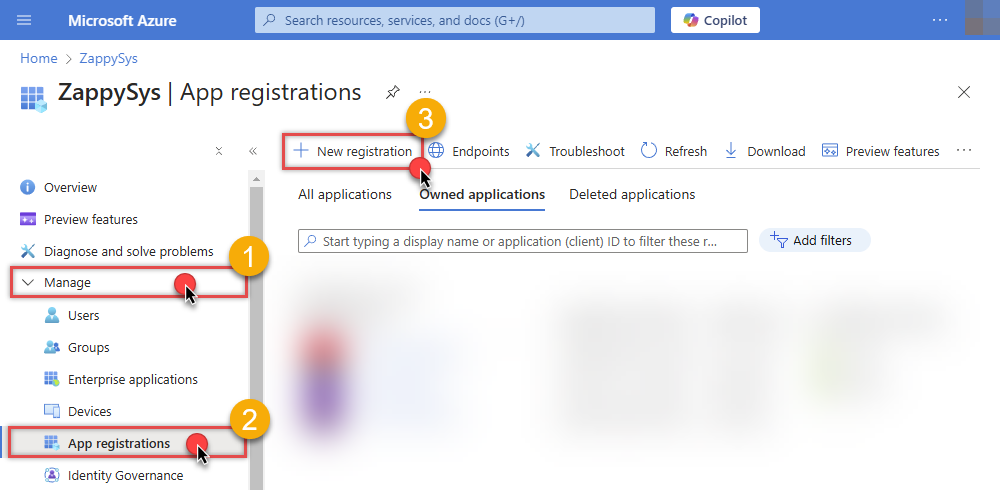
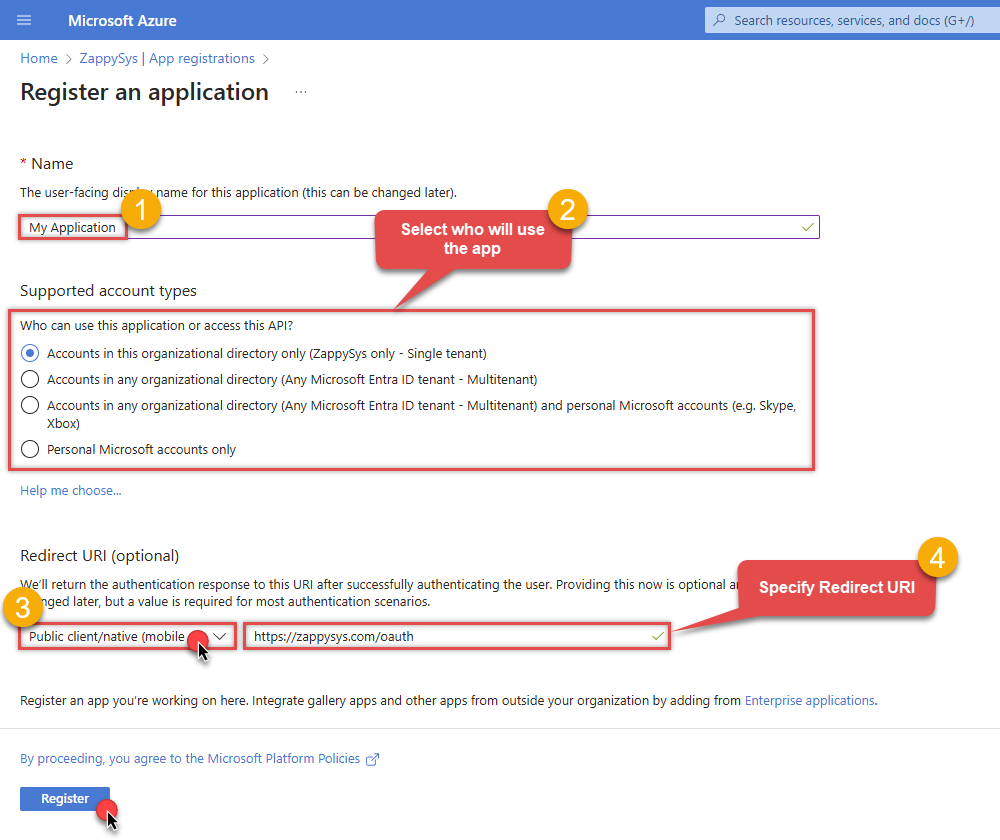
Register a new application by going to
App registrations
and clicking on New registration button:
 INFO: Find more information on how to register an application in Graph API reference.
INFO: Find more information on how to register an application in Graph API reference. -
When configuration window opens, configure these fields:
-
Supported account type
- Use
Accounts in this organizational directory only, if you need access to data in your organization only.
- Use
-
Supported account type
-
Redirect URI:
- Set the type to
Public client/native (mobile & desktop). - Use
https://zappysys.com/oauthas the URL.
- Set the type to
-
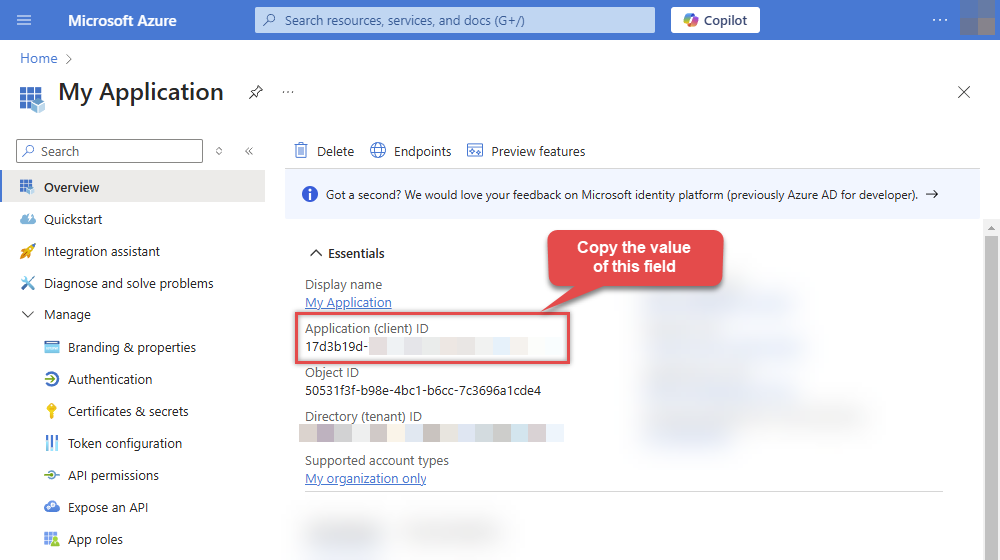
After registering the app, copy the Application (client) ID for later:
-
Then copy OAuth authorization endpoint (v2) & OAuth token endpoint (v2) URLs to use later in the configuration:
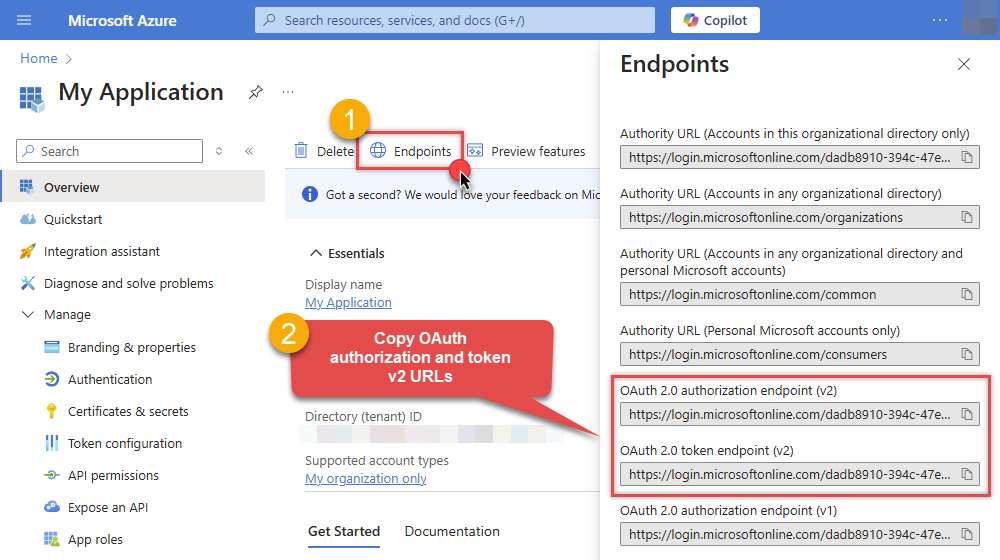
-
Now go to SSIS package or ODBC data source and use the copied values in User Credentials authentication configuration:
- In the Authorization URL field paste the OAuth authorization endpoint (v2) URL value you copied in the previous step.
- In the Token URL field paste the OAuth token endpoint (v2) URL value you copied in the previous step.
- In the Client ID field paste the Application (client) ID value you copied in the previous step.
-
In the Scope field use the default value or select individual scopes, e.g.:
-
email -
offline_access -
openid -
profile -
User.Read -
Files.Read.All -
Files.ReadWrite.All
-
- Press Generate Token button to generate Access and Refresh Tokens.
- Optional step. Choose Default Drive Id from the drop down menu.
- Click Test Connection to confirm the connection is working.
- Done! Now you are ready to use the API Connector!
API Connection Manager configuration
Just perform these simple steps to finish authentication configuration:
-
Set Authentication Type to
User Credentials [OAuth] - Optional step. Modify API Base URL if needed (in most cases default will work).
- Fill in all the required parameters and set optional parameters if needed.
- Press Generate Token button to generate the tokens.
- Finally, hit OK button:
OneDriveUser Credentials [OAuth]https://graph.microsoft.com/v1.0Required Parameters Authorization URL Fill-in the parameter... Token URL Fill-in the parameter... Client ID Fill-in the parameter... Scope Fill-in the parameter... Optional Parameters Client Secret Refresh Token File Path Return URL https://zappysys.com/oauth Default Group or User Id (additional Scopes needed to list - If fails enter manually) Default Drive Id (Select after clicking **Generate Token**) me RetryMode RetryWhenStatusCodeMatch RetryStatusCodeList 429|503|423 RetryCountMax 5 RetryMultiplyWaitTime True Login Prompt Option Search Option For Non-Indexed Fields (Default=Blank - Search Only Indexed) Extra Headers (e.g. Header1:AAA||Header2:BBB) IsAppCred 0 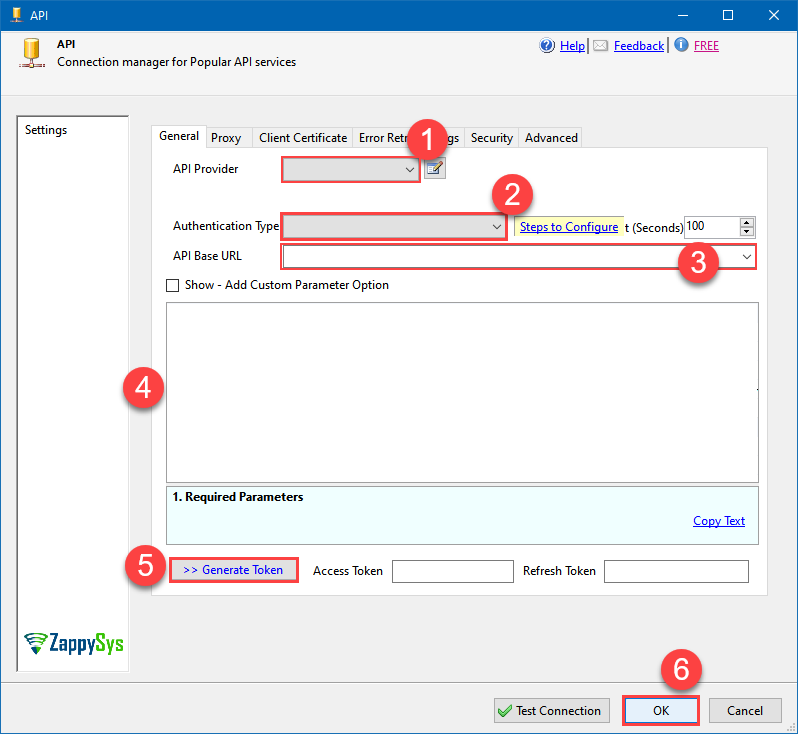
OneDrive authentication
Application-only access is broader and more powerful than delegated access (User Credentials), so you should only use app-only access where needed. Use it when: 1. The application needs to run in an automated way, without user input (for example, a daily script that checks emails from certain contacts and sends automated responses). 2. The application needs to access resources belonging to multiple different users (for example, a backup or data loss prevention app might need to retrieve messages from many different chat channels, each with different participants). 3. You find yourself tempted to store credentials locally and allow the app to sign in 'as' the user or admin. [API reference]
Follow these simple steps below to create Microsoft Entra ID application with application access permissions. Using following steps, you can grant very granular app permissions to access File(s). Choose permission based on your need.
Create OAuth app
- Navigate to the Azure Portal and log in using your credentials.
- Access Microsoft Entra ID.
-
Register a new application by going to
App registrations
and clicking on New registration button:
 INFO: Find more information on how to register an application in Graph API reference.
INFO: Find more information on how to register an application in Graph API reference. -
When configuration window opens, configure these fields:
-
Supported account type
- e.g. select
Accounts in this organizational directory onlyif you need access to data in your organization only.
- e.g. select
-
Supported account type
-
Redirect URI:
- Set the type to
Public client/native (mobile & desktop). - Leave the URL field empty.
- Set the type to
-
After registering the app, copy the Application (client) ID for later:

-
Then copy OAuth authorization endpoint (v2) & OAuth token endpoint (v2) URLs:

-
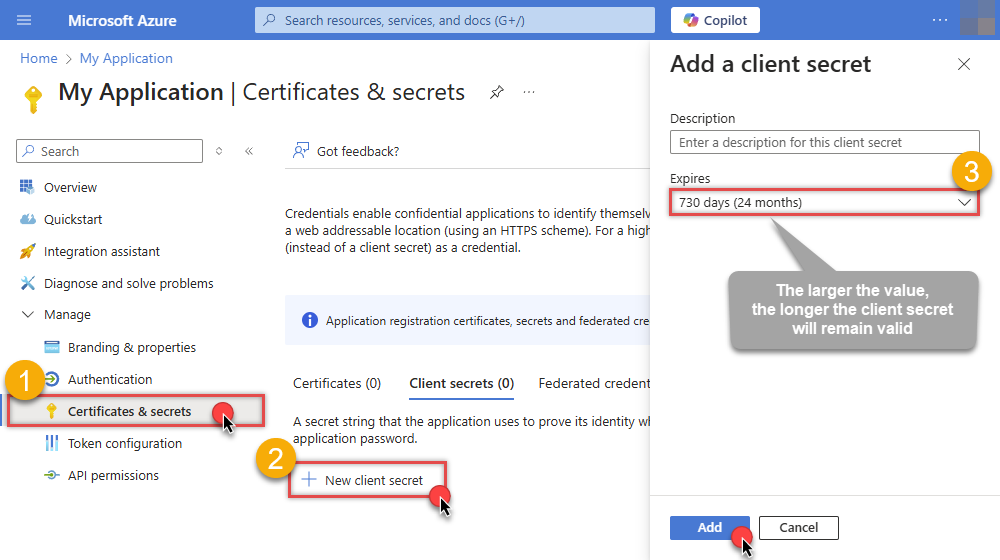
Continue and create Client secret:
-
Then copy the Client secret for later steps:
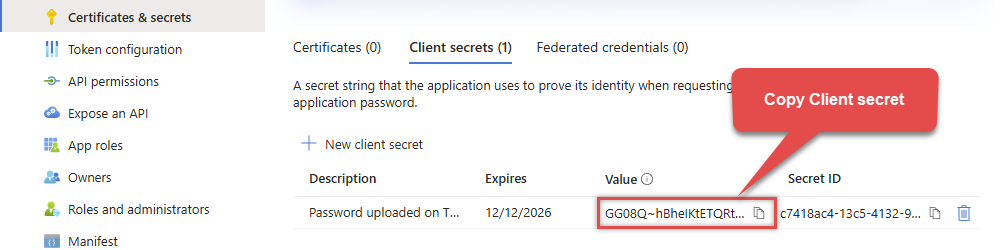
-
Continue by adding permissions for the app by going to the API permissions section, and clicking on Add a permission:
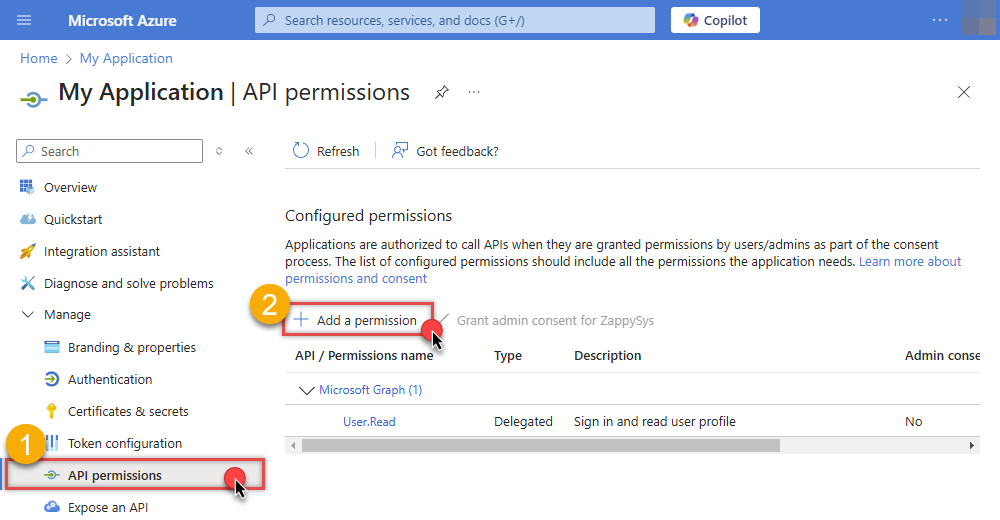
-
Select Microsoft Graph:
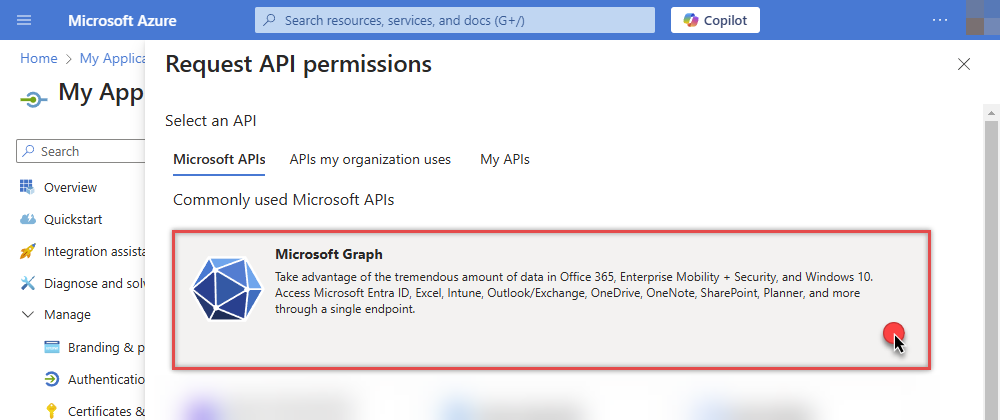
-
Then choose Application permissions option:
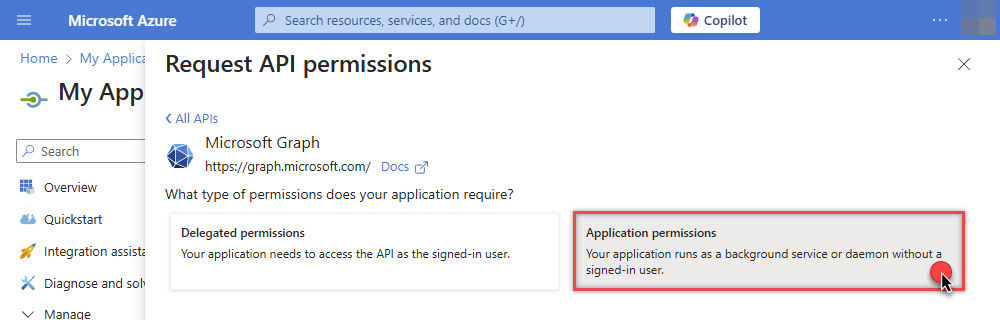
-
Continue by adding these Files (OneDrive) permissions (Just search for "Files" and then select desired permissions):
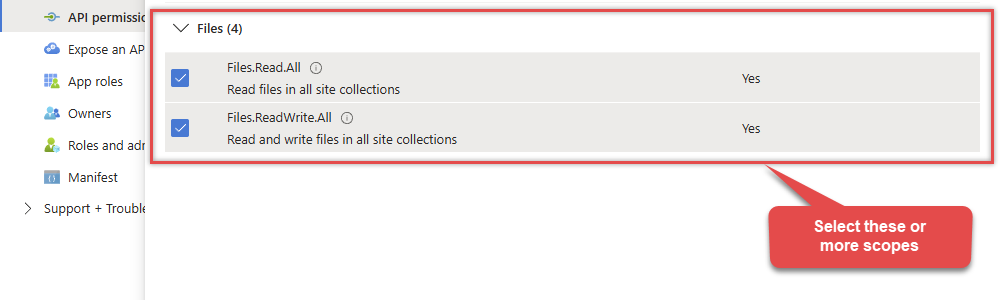
-
Finish by clicking Add permissions button:

-
Now it's time to Grant admin consent for your application:
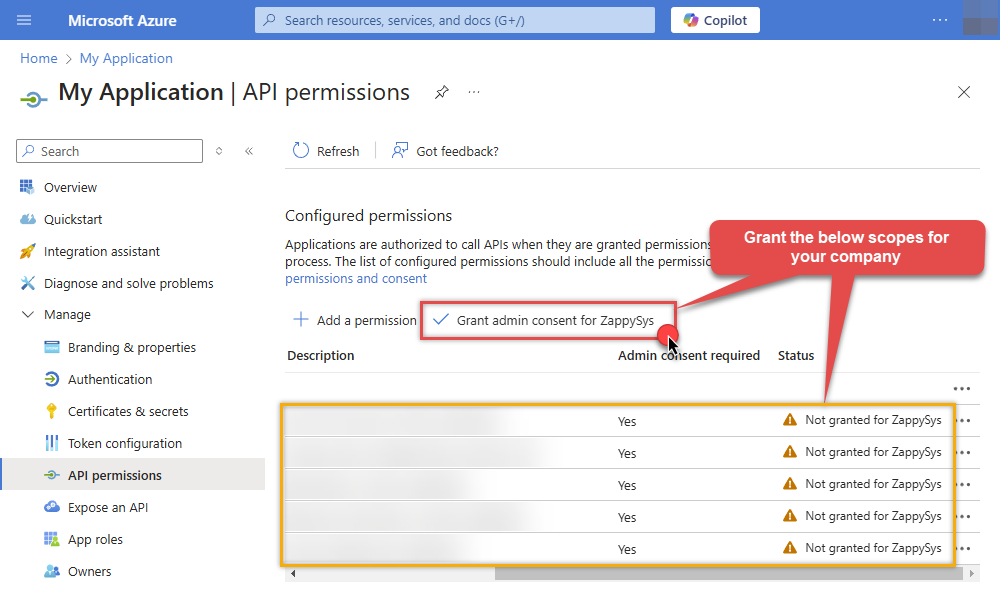
-
Confirm all the permissions are granted:
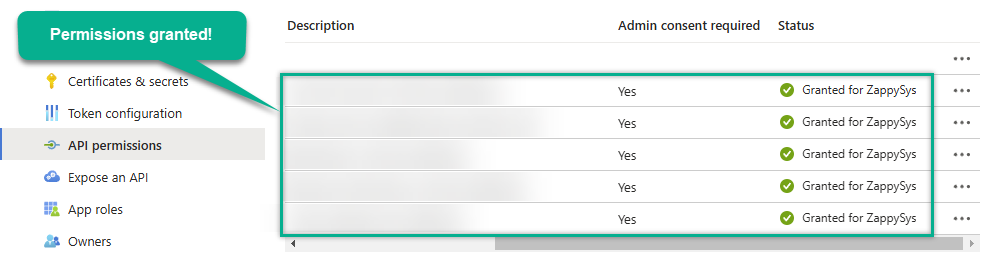
-
Now go to SSIS package or ODBC data source and use the copied values in Application Credentials authentication configuration:
- In the Token URL field paste the OAuth token endpoint (v2) URL value you copied in the previous step.
- In the Client ID field paste the Application (client) ID value you copied in the previous step.
- In the Client Secret field paste the Client secret value you copied in the previous step.
- Optional step. Choose Default Drive Id from the drop down menu.
- Click Test Connection to confirm the connection is working.

API Connection Manager configuration
Just perform these simple steps to finish authentication configuration:
-
Set Authentication Type to
Application Credentials [OAuth] - Optional step. Modify API Base URL if needed (in most cases default will work).
- Fill in all the required parameters and set optional parameters if needed.
- Finally, hit OK button:
OneDriveApplication Credentials [OAuth]https://graph.microsoft.com/v1.0Required Parameters Token URL Fill-in the parameter... Client ID Fill-in the parameter... Client Secret Fill-in the parameter... Default Group or User Id (additional Scopes needed to list - If fails enter manually) Fill-in the parameter... Default Drive Id Fill-in the parameter... Optional Parameters Scope https://graph.microsoft.com/.default RetryMode RetryWhenStatusCodeMatch RetryStatusCodeList 429|503|423 RetryCountMax 5 RetryMultiplyWaitTime True Search Option For Non-Indexed Fields (Default=Blank - Search Only Indexed) Extra Headers (e.g. Header1:AAA||Header2:BBB) IsAppCred 1 
OneDrive authentication
Similar to Assplication-only access but with JWT sign with Private Key [API reference]
Follow these simple steps below to create Microsoft Entra ID application with application access permissions. Using following steps, you can grant very granular app permissions to access File(s). Choose permission based on your need.
Create OAuth app
- Navigate to the Azure Portal and log in using your credentials.
- Access Microsoft Entra ID.
-
Register a new application by going to
App registrations
and clicking on New registration button:
 INFO: Find more information on how to register an application in Graph API reference.
INFO: Find more information on how to register an application in Graph API reference. -
When configuration window opens, configure these fields:
-
Supported account type
- e.g. select
Accounts in this organizational directory onlyif you need access to data in your organization only.
- e.g. select

-
Supported account type
-
After registering the app, copy the Application (client) ID for later:

-
Then copy OAuth authorization endpoint (v2) & OAuth token endpoint (v2) URLs:

Configure App Permissions
-
Continue by adding permissions for the app by going to the API permissions section, and clicking on Add a permission:

-
Select Microsoft Graph:

-
Then choose Application permissions option:

-
Continue by adding these Files (OneDrive) permissions (Just search for "Files" and then select desired permissions):

-
Finish by clicking Add permissions button:

-
Now it's time to Grant admin consent for your application:

-
Confirm all the permissions are granted:

Generate a Self-Signed Certificate
Now let's go through setting up a certificate-based authentication flow for Microsoft Graph or other Azure AD protected APIs using client credentials and a JWT.
You can use OpenSSL or any other way to generate Certificate file but to make it simple we will use below example PowerShell script.
Open PowerShell and execute code listed in below steps.
# Run this in PowerShell #Change .AddYears(1) to desired number. By default it expires certificate in one year as per below code. $cert = New-SelfSignedCertificate ` -Subject "CN=MyClientAppCert" ` -KeySpec Signature ` -KeyExportPolicy Exportable ` -KeyLength 2048 ` -CertStoreLocation "Cert:\CurrentUser\My" ` -KeyAlgorithm RSA ` -HashAlgorithm SHA256 ` -NotAfter (Get-Date).AddYears(1) ` -Provider "Microsoft Enhanced RSA and AES Cryptographic Provider" # Export private key (.pfx) - Keep this with you to make API calls (SECRET KEY - DONOT SHARE) $pfxPath = "$env:USERPROFILE\Desktop\private_key.pfx" $pwd = ConvertTo-SecureString -String "yourStrongPassword123" -Force -AsPlainText Export-PfxCertificate -Cert $cert -FilePath $pfxPath -Password $pwd # Export public certificate (.cer) - UPLOAD this to Azure Portal $cerPath = "$env:USERPROFILE\Desktop\public_key.cer" Export-Certificate -Cert $cert -FilePath $cerPathUpload the Certificate (i.e. Public Key *.cer)
Once we have certificate file generated.- In your App Registration, go to Certificates & secrets
- Under Certificates, click Upload certificate
- Select the
.cerfile (public certificate)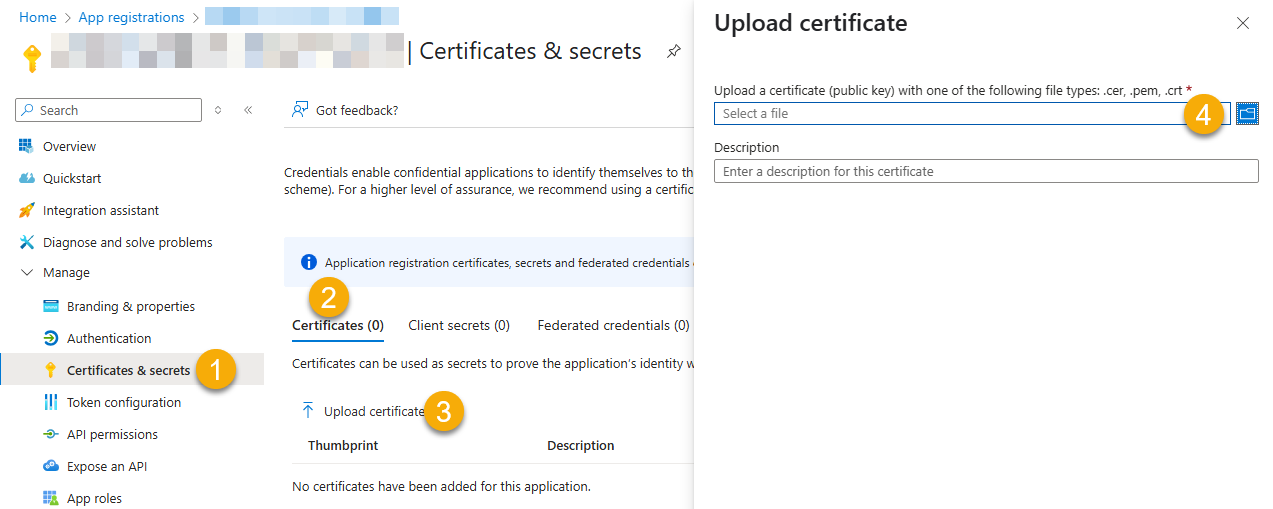
- Click Select a file (Browse button)
- Select public key file (*.cer) from local machine and click OK to upload
Configure ZappySys Connection - Use private key (i.e. *.pfx or *.pem)
Now its time to use certificate pfx file (private key) generated in the previous step (NOTE: PFX file contains both private key and public key).-
Go to SSIS package or ODBC data source and use the copied values in Application Credentials authentication configuration:
- In the Token URL field paste the OAuth token endpoint (v2) URL value you copied in the previous step.
- In the Client ID field paste the Application (client) ID value you copied in the previous step.
- Configure private key
- go to
Certificate Tab - Change Storage Mode to
Disk File: *.pfx format (PKCS#12).NOTE: You can also useStored In LocalMachinemode if PFX file already imported in the Local Certificate Storage Area - User Store OR Machine Store. If you used OpenSSL to generate key pair then useDisk File: *.pem format (PKCS#8 or PKCS#1)Mode for Cert Store Location. - Supply the key file path
- Supply the certificate password (same password used in earlier PowerShell script)
- go to
- Now go back to General Tab, choose Default Group / User Id and Default Drive Id from the drop down menu.
- Click Test connection see everything is good
API Connection Manager configuration
Just perform these simple steps to finish authentication configuration:
-
Set Authentication Type to
Application Credentials with Certificate (Sign JWT with Private Key) [OAuth] - Optional step. Modify API Base URL if needed (in most cases default will work).
- Fill in all the required parameters and set optional parameters if needed.
- Finally, hit OK button:
OneDriveApplication Credentials with Certificate (Sign JWT with Private Key) [OAuth]https://graph.microsoft.com/v1.0Required Parameters Token URL Fill-in the parameter... Client ID Fill-in the parameter... Certificate: *** Configure [Client Certificate] Tab *** Fill-in the parameter... Default Group or User Id (additional Scopes needed to list - If fails enter manually) Fill-in the parameter... Default Drive Id Fill-in the parameter... Optional Parameters RetryMode RetryWhenStatusCodeMatch RetryStatusCodeList 429|503|423 RetryCountMax 5 RetryMultiplyWaitTime True Search Option For Non-Indexed Fields (Default=Blank - Search Only Indexed) Extra Headers (e.g. Header1:AAA||Header2:BBB) IsAppCred 1 
-
Select the desired endpoint, change/pass the properties values, and click on Preview Data button to make the API call.
API Source - OneDriveOneDrive Connector can be used to integrate OneDrive and your defined data source, e.g. Microsoft SQL, Oracle, Excel, Power BI, etc. Get, write, delete OneDrive data in a few clicks!
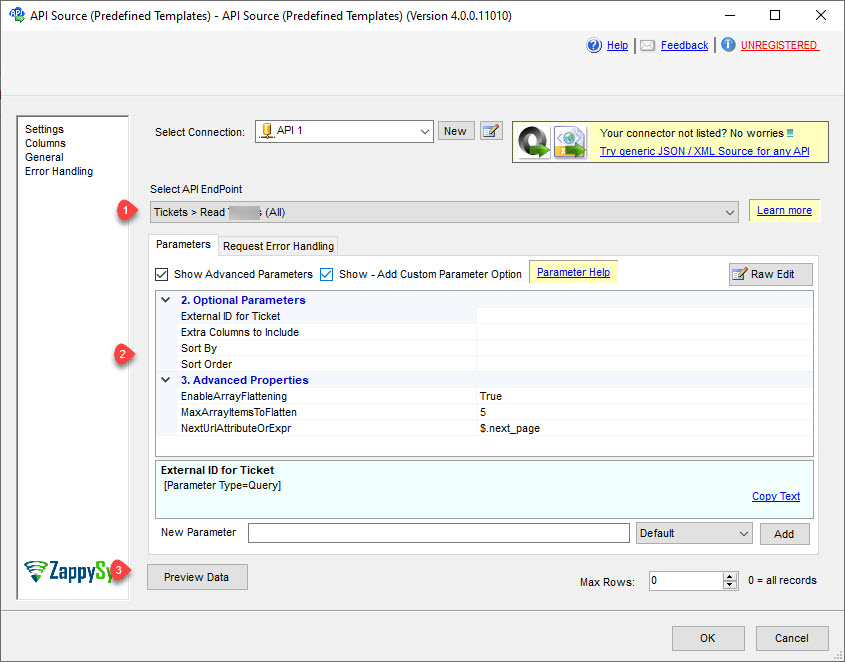
-
That's it! We are done! Just in a few clicks we configured the call to OneDrive using OneDrive Connector.
You can load the source data into your desired destination using the Upsert Destination , which supports SQL Server, PostgreSQL, and Amazon Redshift. We also offer other destinations such as CSV , Excel , Azure Table , Salesforce , and more . You can check out our SSIS PowerPack Tasks and components for more options. (*loaded in Trash Destination)