Authentication User Credentials
Description
Use delegated access (User Credentials) whenever you want to let a signed-in user work with their own resources or resources they can access. Whether it's an admin setting up policies for their entire organization or a user deleting an email in their inbox, all scenarios involving user actions should use delegated access. [API reference]
Instructions
Follow these simple steps below to create Microsoft Entra ID application with delegated access:
automation@my-company.com).
When you use a personal account which is tied to a specific employee profile and that employee leaves the company,
the token may become invalid and any automated processes using that token will start to fail.
- Navigate to the Azure Portal and log in using your credentials.
- Access Microsoft Entra ID.
-
Register a new application by going to
App registrations
and clicking on New registration button:
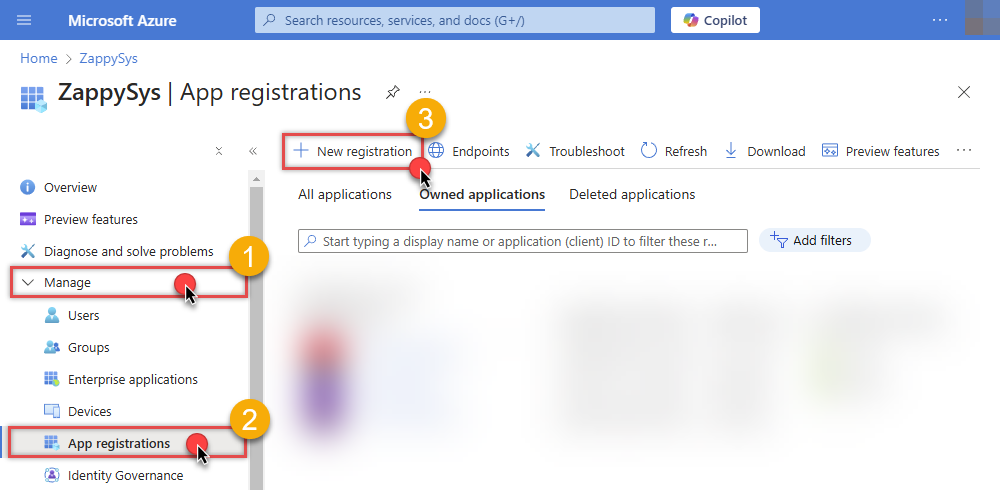 INFO: Find more information on how to register an application in Graph API reference.
INFO: Find more information on how to register an application in Graph API reference. -
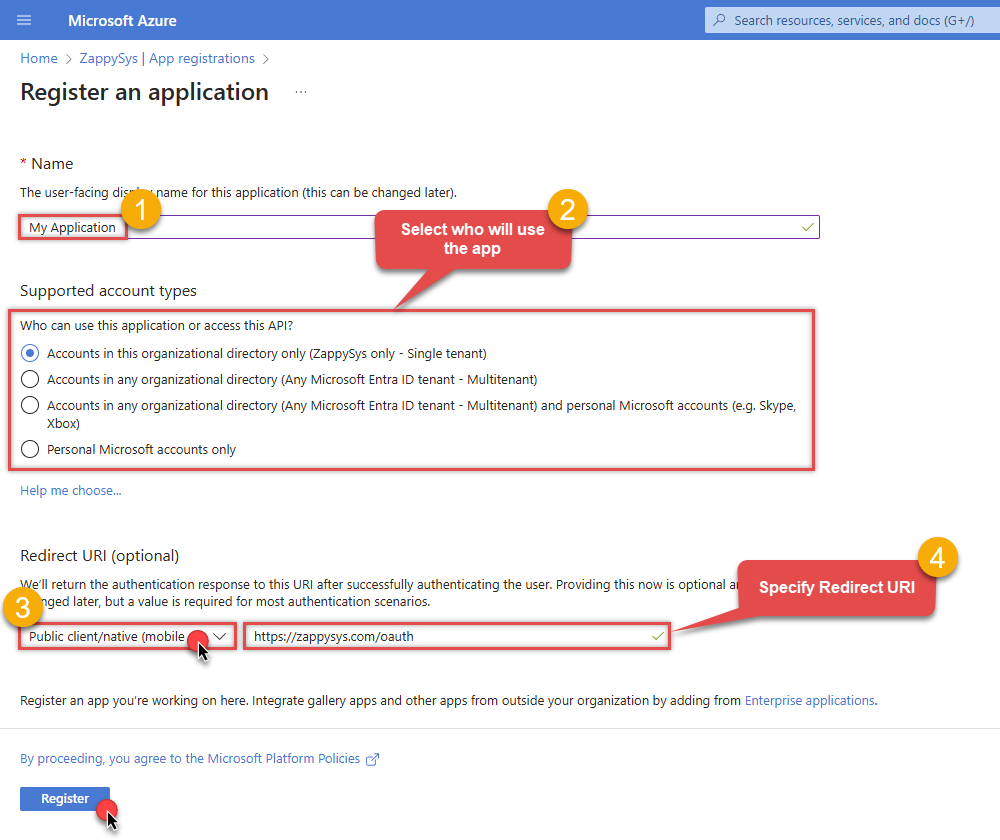
When configuration window opens, configure these fields:
-
Supported account type
- Use
Accounts in this organizational directory only, if you need access to data in your organization only.
- Use
-
Supported account type
-
Redirect URI:
- Set the type to
Public client/native (mobile & desktop). - Use
https://zappysys.com/oauthas the URL.
- Set the type to
-
After registering the app, copy the Application (client) ID for later:
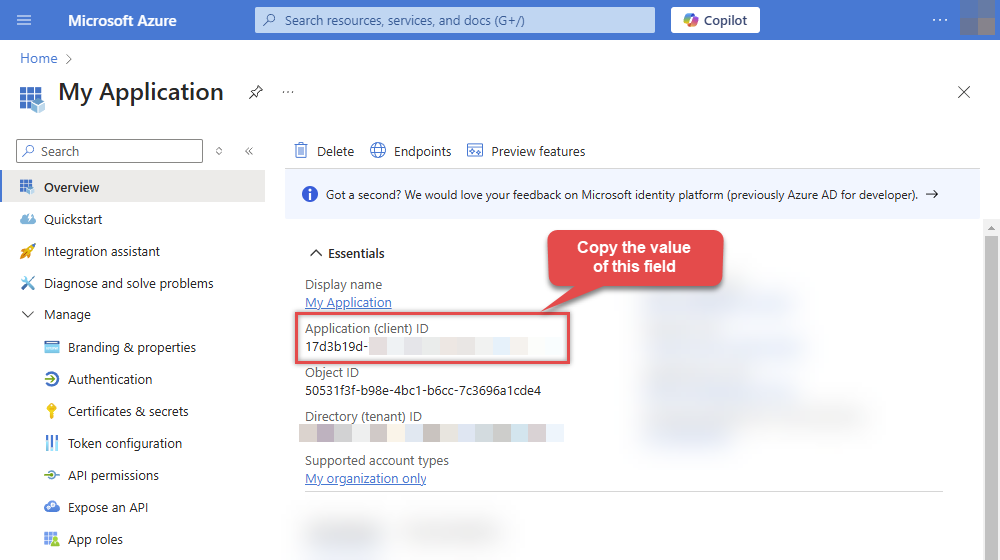
-
Then copy OAuth authorization endpoint (v2) & OAuth token endpoint (v2) URLs to use later in the configuration:
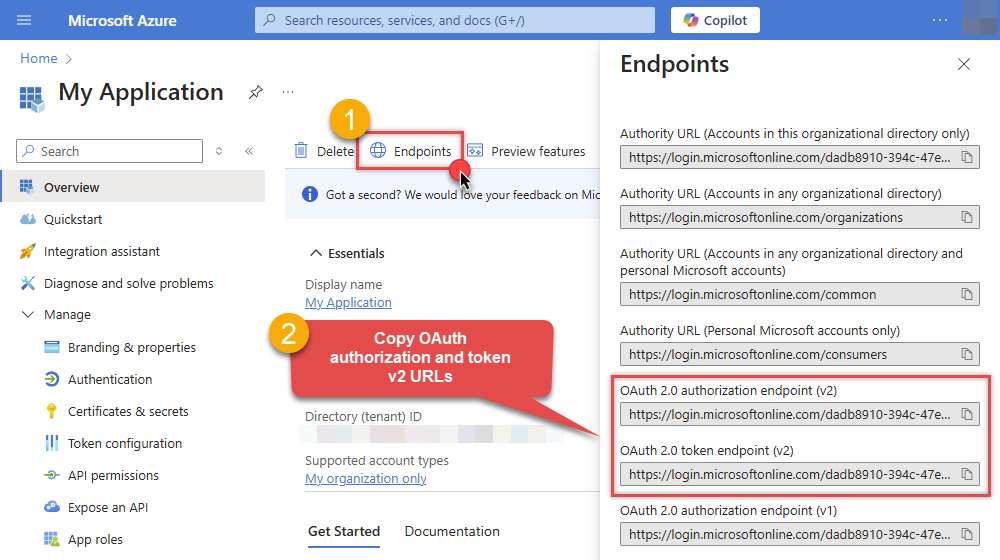
-
Now go to SSIS package or ODBC data source and use the copied values in User Credentials authentication configuration:
- In the Authorization URL field paste the OAuth authorization endpoint (v2) URL value you copied in the previous step.
- In the Token URL field paste the OAuth token endpoint (v2) URL value you copied in the previous step.
- In the Client ID field paste the Application (client) ID value you copied in the previous step.
-
In the Scope field use the default value or select individual scopes, e.g.:
-
email -
offline_access -
openid -
profile -
Mail.Read -
Mail.Read.Shared -
Mail.ReadBasic -
Mail.ReadBasic.Shared -
Mail.ReadWrite -
Mail.ReadWrite.Shared -
Mail.Send -
Mail.Send.Shared -
User.Read -
User.ReadBasic.All -
Group.Read.All
-
- Press Generate Token button to generate Access and Refresh Tokens.
- Optional step. Choose Default User Id from the drop down menu (if someone shared a mailbox with you).
- Click Test Connection to confirm the connection is working.
- Done! Now you are ready to use the API Connector!
Parameters
| Parameter | Required | Default value | Options | ||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
Name:
Label: Authorization URL |
YES |
|
|||||||||||||||||||||||||||||||||
|
Name:
Label: Token URL |
YES |
|
|||||||||||||||||||||||||||||||||
|
Name:
Label: Client ID |
YES | ||||||||||||||||||||||||||||||||||
|
Name:
Label: Scope Permissions you want to use. |
YES |
offline_access~email~Mail.Read~Mail.Read.Shared~Mail.ReadBasic~Mail.ReadBasic.Shared~openid~profile~User.Read~User.ReadBasic.All~Group.Read.All~Mail.ReadWrite~Mail.ReadWrite.Shared~Mail.Send~Mail.Send.Shared~
|
|
||||||||||||||||||||||||||||||||
|
Name:
Label: Return URL |
YES |
https://zappysys.com/oauth
|
|
||||||||||||||||||||||||||||||||
|
Name:
Label: Client Secret |
|||||||||||||||||||||||||||||||||||
|
Name:
Label: Refresh Token File Path If you cant fit long refresh token in ConnectionString from your program then use this. Supply three properties in json format (i.e. save this in file { "access_token": "YOUR_ACCESS_TOKEN", "refresh_token": "YOUR_REFRESH_TOKEN", "expires_in": 3600 } ) |
|||||||||||||||||||||||||||||||||||
|
Name:
Label: Login Prompt Option Choose this if you want to force login prompt or permission prompt. |
|
||||||||||||||||||||||||||||||||||
|
Name:
Label: Default User Id (Select after clicking **Generate Token**) The Microsoft Mail user ID GUID or email address for the account to read messages from. (Examples: '4ff54a77-9c09-4274-958f-83bdc0a53900' or 'first.last@domain.com') |
me
|
||||||||||||||||||||||||||||||||||
|
Name:
Label: RetryMode |
RetryWhenStatusCodeMatch
|
|
|||||||||||||||||||||||||||||||||
|
Name:
Label: RetryStatusCodeList |
429|503
|
||||||||||||||||||||||||||||||||||
|
Name:
Label: RetryCountMax |
5
|
||||||||||||||||||||||||||||||||||
|
Name:
Label: RetryMultiplyWaitTime |
True
|
